MCP OAuth Integration: Secure GitHub Authentication for Docker Toolkit
Docker MCP Toolkit adds OAuth support and streamlined Integration with GitHub and VS Code
A recent MCP Reddit poll revealed that indirect prompt injection is seen as the biggest security threat to Model Context Protocol (MCP) implementations - but there's another critical vulnerability flying under the radar.

The Problem with OAuth Flow Management
Without a centralized gateway, each MCP server that needs authentication (like Firecrawl for web scraping, GitHub for code access, or Microsoft for document processing) has to implement its own complete authentication flow.
This means if you have three different MCP servers that need Firecrawl API access, you end up managing Firecrawl API keys three separate times - once for your web scraping server, once for your content analysis server, and once for your research server. Each server manages its own API credentials independently, handles rate limiting on its own, and stores secrets in different ways.
You might have one server storing Firecrawl API keys in a local file, another keeping GitHub tokens in environment variables, and a third managing authentication in a database.
# You need separate credentials for each server
export FIRECRAWL_API_KEY_1="fc-123abc-server1"
export GITHUB_TOKEN_1="ghp_456def-server1"
export FIRECRAWL_API_KEY_2="fc-789ghi-server2"
export GITHUB_TOKEN_2="ghp_012jkl-server2"
# Server 3 uses config files instead
echo '{
"firecrawl": {"api_key": "fc-345mno-server3"},
"github": {"personal_access_token": "ghp_678pqr-server3"}
}' > config.json How Docker Solves this Problem
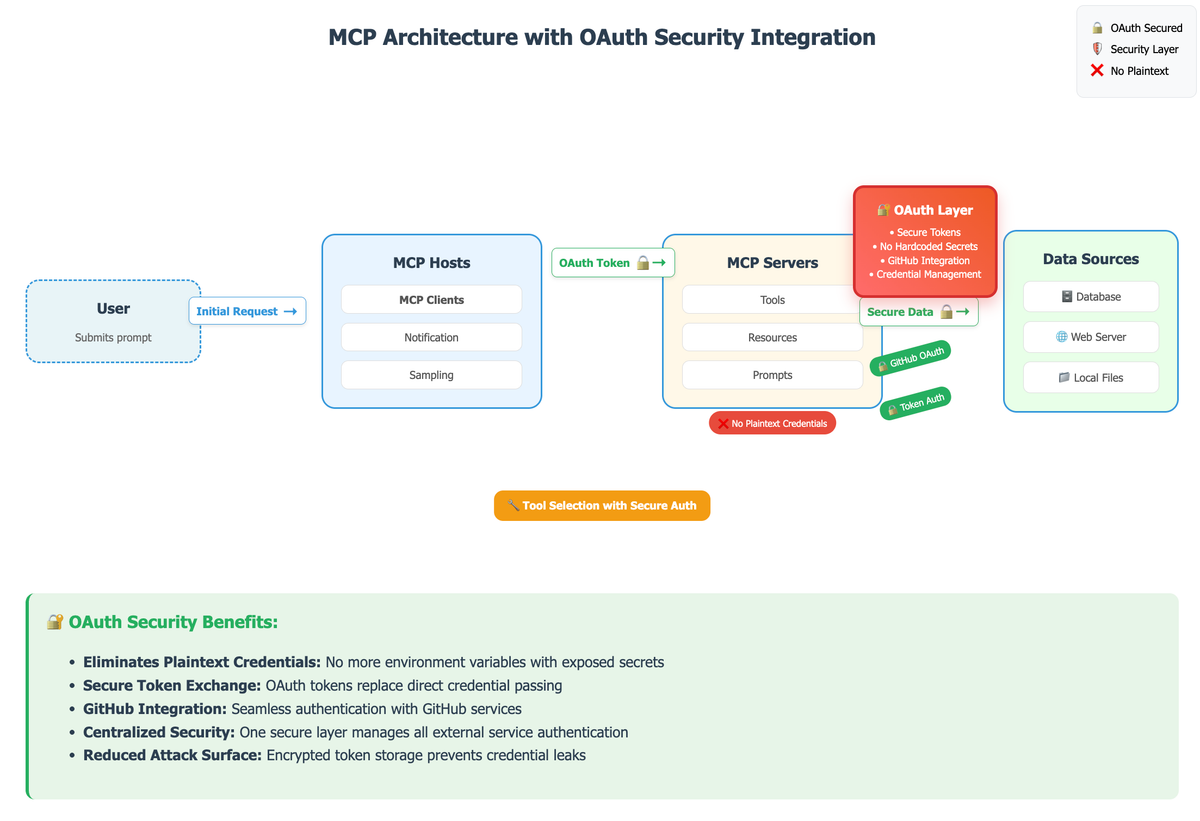
We're addressing this head-on with the Docker MCP Toolkit's secure credential storage system. No more hardcoded secrets, no more plaintext exposure.
We're rolling out OAuth support, starting with GitHub integration. This means developers can now authenticate with MCP servers and third-party services securely, without compromising their credentials.
To set up your GitHub MCP server, go to the OAuth tab, connect your GitHub account, enable the server, and authorize OAuth for secure authentication.

Introducing the new CLI for OAuth
Here's the main OAuth Command Structure:
➜ ~ docker mcp oauth --help
Docker MCP Toolkit's CLI - Manage your MCP servers and clients.
Usage: docker mcp oauth
Available Commands:
authorize
ls List available OAuth apps.
revoke
➜ ~ Available OAuth Subcommands:
1. 📋 List OAuth Apps
➜ ~ docker mcp oauth ls
gdrive | not authorized
github | authorized - Purpose: Lists all available OAuth applications and their authorization status
- Options: --json: Output results in JSON format
- Output: Shows app name and authorization status (authorized/not authorized)
2. 🔓 Authorize OAuth App
➜ ~ docker mcp oauth authorize github
Opening your browser for authentication. If it doesn't open automatically, please visit:
➜ ~ - Purpose: Initiates OAuth authorization flow for a specific application
- Process: Opens browser for authentication or provides URL for manual authentication
- Example: docker mcp oauth authorize github
3. ❌ Revoke OAuth Authorization
docker mcp oauth revoke <app>- Purpose: Revokes OAuth authorization for a specific application
- Result: Removes stored OAuth credentials for the specified app
Key Features:
- 🔒 Secure Token Storage: OAuth tokens are managed through Docker Desktop's secure credential storage
- 🌐 Browser Integration: Automatic browser opening for OAuth flows
- 📱 App Management: Easy authorization and revocation of multiple OAuth apps
- 🔄 Status Tracking: Clear visibility of which apps are authorized
Integration with MCP Servers
The OAuth commands work seamlessly with MCP servers that require OAuth authentication, particularly for:
- GitHub integration (as mentioned in your original post)
- Third-party API services
- Cloud service providers
This OAuth implementation eliminates the need for plaintext credentials in environment variables by using secure token-based authentication managed through Docker Desktop's credential store.
Security shouldn't be an afterthought in AI development workflows. As we build more sophisticated AI tools, we need infrastructure that prioritizes security from day one.
What security practices do you prioritize in your AI development stack?
Further Reading
- https://www.docker.com/blog/docker-mcp-catalog-secure-way-to-discover-and-run-mcp-servers/
- https://www.docker.com/blog/docker-mcp-gateway-secure-infrastructure-for-agentic-ai/
- https://www.docker.com/blog/mcp-server-best-practices/
#MCP #AISecurity #DeveloperTools #OAuth #GitHub #Security #AI #DevOps #MachineLearning