Docker Hardened Images: The Complete Guide to Secure, Minimal Container Images for Production
Learn everything about Docker Hardened Images (DHIs) - secure, minimal, production-ready container images that reduce vulnerabilities by 95%, ensure compliance, and integrate seamlessly into existing workflows.
Last week, I was chatting with a DevSecOps engineer during a Meetup event who told me their traditional Ubuntu-based containers had over 200 CVEs. Yikes! That's exactly why I'm excited to talk about Docker Hardened Images (DHIs) today. Trust me, once you understand what these bad boys can do, you'll wonder how you ever lived without them.
So, What Exactly Are Docker Hardened Images?
Let me break it down for you in simple terms.
Remember when we used to build containers by starting with a full Linux distribution and then trying to remove stuff we didn't need? It was like buying a fully loaded car and then removing the seats you don't use. Doesn't make much sense, right?
Docker Hardened Images flip this approach completely. They're minimal, secure, production-ready container images that Docker maintains directly. Think of them as containers that went to the gym, lost all the unnecessary fat, and came out lean, mean, and secure.

Here's what makes them special:
- Near-zero exploitable CVEs (yes, you read that right!)
- No shells, no package managers - if an attacker gets in, they've got nothing to work with
- Continuously updated - Docker handles the patching, so you don't have to
- Built for production from day one
The Real Problem We're Solving Here
Let's be honest - container security is a mess for most organizations. I recently helped a fintech startup audit their container images, and here's what we found:
Their Node.js application container had:
- 247 known vulnerabilities
- A 450MB image size (for a 50MB app!)
- Shell access that nobody ever used
- Package managers that were attack vectors waiting to happen
Sound familiar?
This is the reality for most teams. You're shipping containers with hundreds of potential security holes, and you're spending countless hours trying to patch them. It's exhausting, and frankly, it's not sustainable.
Why DHIs Are Different (And Why You Should Care)
Docker Hardened Images adapt into your workflow – no retooling, no surprises. Built on familiar distros like Alpine and Debian and following a distroless approach, they strip away unneeded components to reduce risk. Unlike other minimal images, DHIs balance security with flexibility, letting you customize with certs, packages, and configs – all on a hardened, verifiable foundation.
The Distroless Revolution

Here's where things get interesting. DHIs use what we call a "distroless" approach. No, that doesn't mean they don't have a Linux distribution - it means they strip away everything except what your app actually needs to run.
Let me show you what I mean:
Traditional Container:
FROM ubuntu:22.04
# Includes: bash, apt, curl, wget, vi, and 500+ other packages
# Attack surface: HUGE
# CVEs: 100-300 typicalDocker Hardened Image:
FROM <your-namespace>/dhi-python:3.11-runtime
# Includes: Python runtime and essential libraries ONLY
# Attack surface: Minimal
# CVEs: Near-zeroThe difference? DHIs reduce your attack surface by up to 95%. That's not marketing fluff - that's real-world results.
SLSA Build Level 3 - The Gold Standard

Now, here's something cool that not many people talk about. DHIs are built to meet SLSA (Supply chain Levels for Software Artifacts) Build Level 3 standards.
What does that mean for you?
- Every image has a tamper-proof build process
- You get complete provenance (know exactly where your image came from)
- Cryptographically signed metadata
- Built-in SBOMs and VEX documents for compliance
Your security team will love you for this. Trust me.
All DHIs are built using SLSA Build Level 3 practices, and each image variant is published with a full set of signed attestations.
Attestations are automatically published and associated with each mirrored DHI in your Docker Hub organization. They can be inspected using tools like Docker Scout or Cosign, and are consumable by CI/CD tooling or security platforms.
DHIs Just Drop Right Into Your CI/CD Pipeline
Here's the beautiful thing about Docker Hardened Images - they work exactly where your current base images work. No special magic required.
Got GitHub Actions? Just swap that base image line. Running GitLab CI/CD? Same deal. Jenkins, CircleCI, Azure DevOps, or that custom pipeline your team built three years ago? DHIs will work there too.
It's literally a one-line change in your Dockerfile, and boom - you're running hardened images through your entire pipeline.
Playing Nice with Your DevSecOps Tools (No Drama!)
Look, I know what you're thinking - "Great, another tool that claims to integrate but actually breaks half my stack."
Not this time, folks.
We actually did our homework here. We, Docker partnered with all the big players to make sure DHIs work smoothly with whatever you've already got running. Your vulnerability scanners, container registries, policy engines - they all understand DHIs out of the box.
The best part? Every single DHI comes loaded with:
- Signed SBOMs - Your security team can finally see what's inside every container
- Live CVE data - Know exactly what vulnerabilities exist (spoiler: usually zero!)
- VEX documents - Understand which vulnerabilities actually matter vs. noise
- SLSA Level 3 provenance - Full chain of custody for compliance audits
And here's the kicker - everything is cryptographically signed and properly structured. That means you can pipe this metadata straight into your policy engines, compliance dashboards, or whatever reporting tools your CISO loves. No parsing nightmares, no custom scripts - it just works.
Your security team gets their audit trails, your compliance folks get their documentation, and you get to ship code without the usual security theater. Everyone wins!
Getting Your Hands Dirty: Implementation Time
Alright, enough theory. Let's see how this works in practice. I'll walk you through migrating a real application to DHIs.
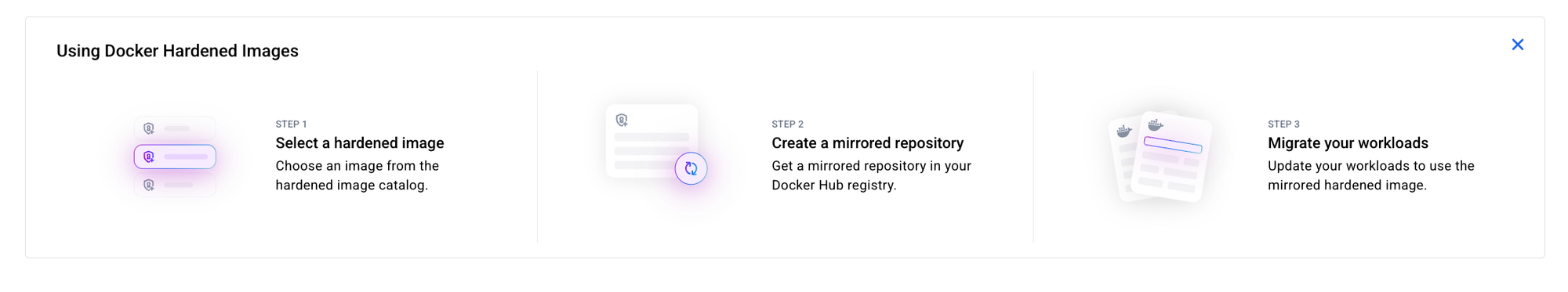
Using Docker Hardened images involve 3 steps process:
- Select a Hardened image
- Create a mirrored repository
- Migrate your workloads
Check What You're Currently Using
First, let's see what you're working with:
docker images --format "table {{.Repository}}\t{{.Tag}}\t{{.Size}}"Shocked by those image sizes? Yeah, I was too.
Step 1: Pick Your DHI
Browse the Docker Hardened image catalog here: https://hub.docker.com/orgs/<your-org>/hardened-images
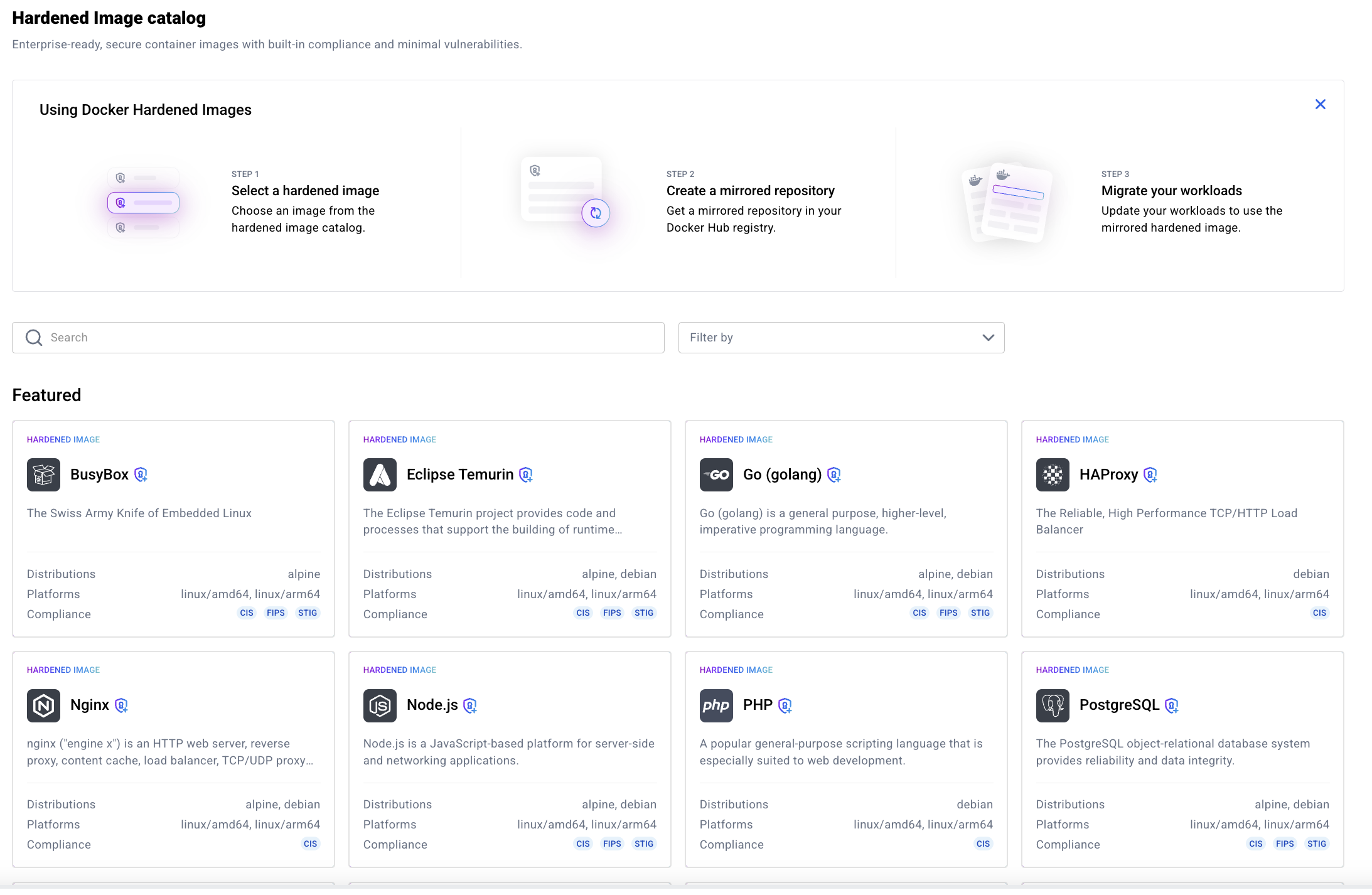
Docker provides hardened images for all major runtimes. Here are the ones I use most:
- Python apps:
docker/dhi-python:3.11-runtime - Node.js apps:
docker/dhi-node:20-runtime - Java apps:
docker/dhi-java:17-runtime - Go apps:
docker/dhi-go:1.21-runtime
Pro tip: Use development variants (-dev) for building, runtime variants (-runtime) for production.
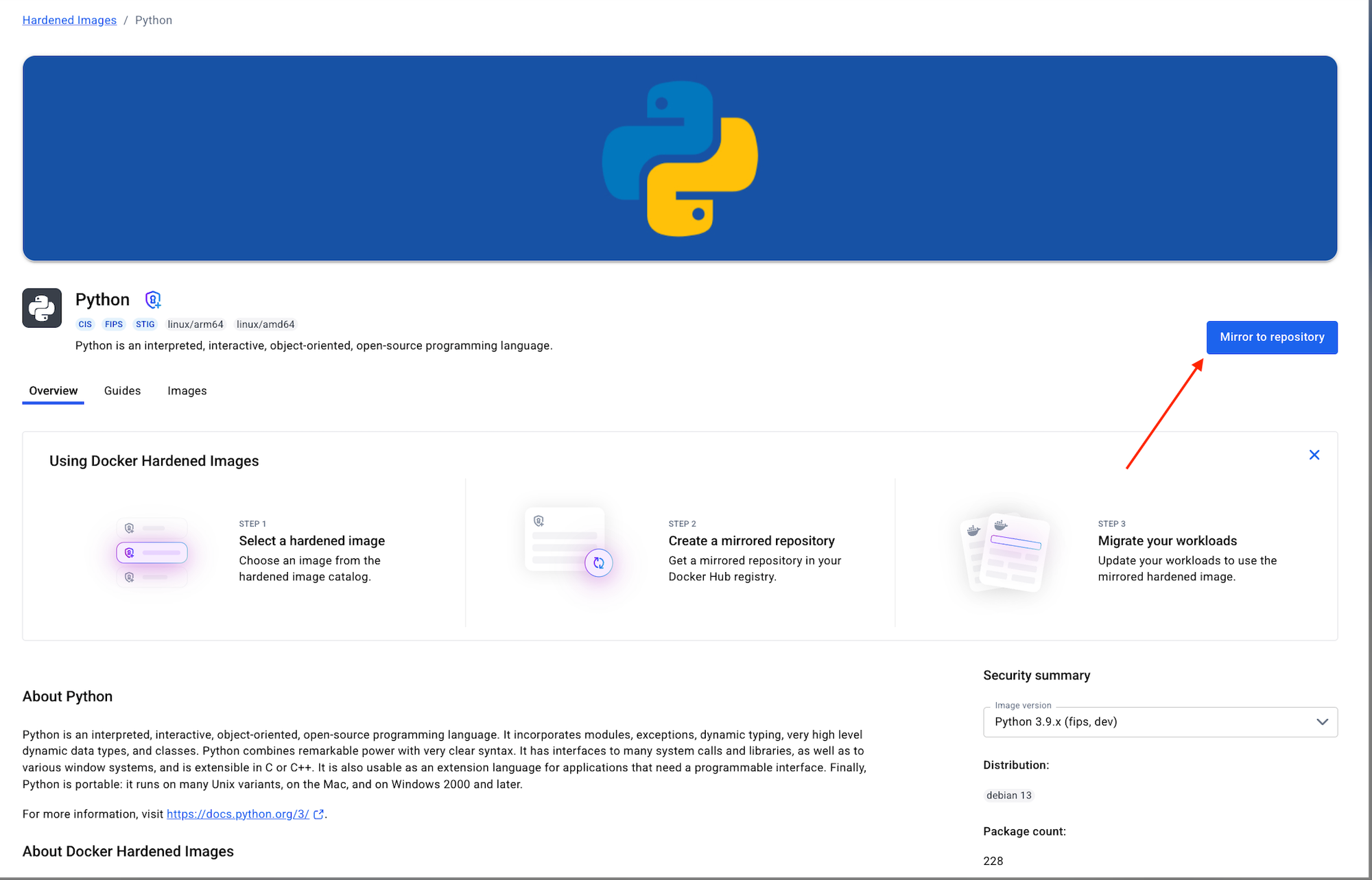
Step 2. Create a mirrored repo
Ensure that you click on "Mirror to repository" to mirror it to your Hub Org.
Select where to mirror the repository, name the destination, and choose which definitions to keep updated.
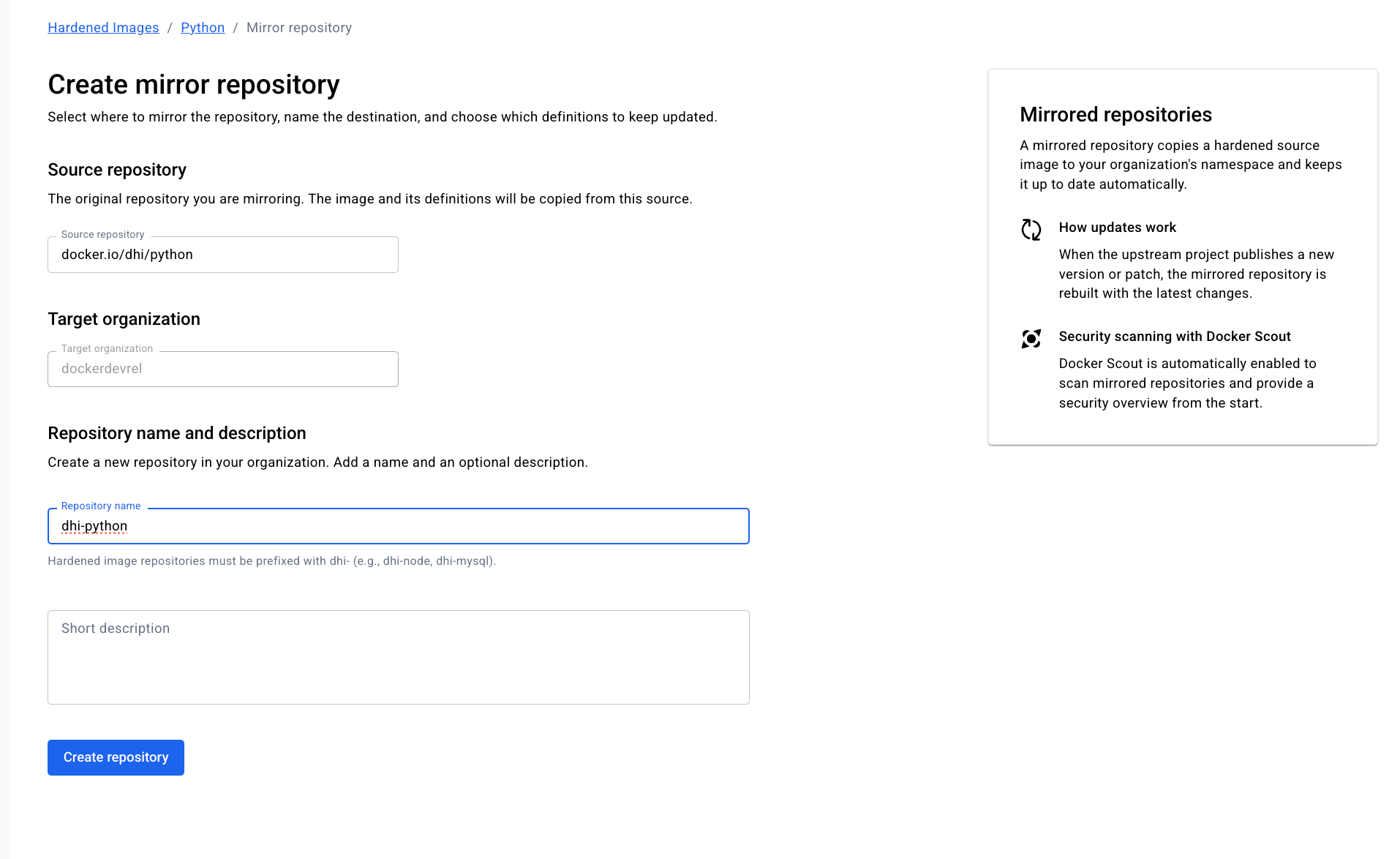
Step 3: The Migration
Let me show you a real migration I did last week for a Python Flask app:
Before (The Old Way):
FROM python:3.11
WORKDIR /app
COPY requirements.txt .
RUN pip install -r requirements.txt
COPY . .
EXPOSE 5000
CMD ["python", "app.py"]
# Image size: 1.2GB
# CVEs: 178After (The DHI Way):
# Build stage
FROM <your-namespace>/dhi-python:<tag> AS runtime
WORKDIR /app
COPY requirements.txt .
RUN pip install --user -r requirements.txt
# Runtime stage
FROM <your-namespace>/dhi-python:<tag> AS runtime
FROM docker/dhi-python:3.11-runtime
WORKDIR /app
COPY --from=builder /root/.local /home/nonroot/.local
COPY --chown=nonroot:nonroot . .
USER nonroot
EXPOSE 5000
CMD ["python", "app.py"]
# Image size: 95MB
# CVEs: 0See the difference? We went from 1.2GB to 95MB and eliminated ALL known CVEs. That's what I call a win!
Getting Started
- Explore available images and metadata in the DHI catalog.
- Mirror trusted images into your namespace or registry.
- Adopt DHIs in your workflows by pulling, using in development and CI, and migrating existing applications to use secure, minimal base images.
- Analyze images by verifying signatures, SBOMs, and provenance, and scanning for vulnerabilities.
- Enforce policies to maintain security and compliance.
- Debug containers based on DHIs without modifying the image.
Real-World Results (From My Own Experience)
I've been working with DHIs for the past few months, helping various companies migrate. Here are some real numbers:
E-commerce Platform (Node.js):
- Image size: 890MB → 67MB (92% reduction)
- CVEs: 234 → 0
- Container startup time: 4.2s → 0.8s
- Monthly AWS costs: Saved $2,400 on ECR storage alone
Financial Services API (Python):
- Image size: 1.1GB → 89MB
- Security audit time: 3 days → 2 hours
- Deployment time: 12 minutes → 3 minutes
IoT Gateway Service (Go):
- Image size: 750MB → 12MB (yes, 12MB!)
- Memory usage: 450MB → 120MB
- Pods per node: Increased from 8 to 25
Common Gotchas and How to Handle Them
Let's be real - migration isn't always smooth sailing. Here are issues I've encountered and how to fix them:
"But I Need to Debug in Production!"
I hear this a lot. Here's the thing - you shouldn't be SSH-ing into production containers anyway. Instead:
- Use proper logging (structured logs FTW!)
- Implement distributed tracing
- Use remote debugging protocols
- For emergencies, use
kubectl debugor similar tools
"My App Won't Start!"
Usually happens because:
- Missing system libraries (add them in build stage)
- Wrong user permissions (use
--chown=nonroot:nonroot) - Hardcoded paths to
/bin/bash(refactor your code)
"The Image Build Takes Forever!"
Multi-stage builds are your friend:
# Cache dependencies separately
FROM docker/dhi-node:20-dev AS deps
COPY package*.json ./
RUN npm ci --only=production
FROM docker/dhi-node:20-runtime
COPY --from=deps node_modules ./node_modules
COPY . .Best Practices I've Learned the Hard Way
After migrating dozens of applications, here's what works:
1. Start with Non-Critical Services
Don't migrate your payment gateway first. Start with that internal dashboard nobody uses on weekends.
2. Use Multi-Stage Builds Always
Seriously, always. It keeps build tools out of production and reduces image size.
3. Test, Test, Test
Create a staging environment that mirrors production. Test everything:
# Quick smoke test script I use
docker run --rm your-dhi-image /bin/sh -c "echo 'If you see this, you have a shell!'"
# Should fail with DHIs!4. Automate Security Scanning
Add this to your CI/CD:
- name: Scan with Docker Scout
run: |
docker scout cves your-image:latest
docker scout compare your-image:latest --to your-image:previous5. Document Everything
Your future self will thank you. Create a migration checklist for your team.
The Bottom Line
Look, I get it. Changing your container strategy feels risky. But here's what I tell everyone who's on the fence:
Would you rather:
- Spend 10 hours migrating to DHIs once, or
- Spend 2 hours every week patching vulnerabilities forever?
The math is simple.
Plus, once you see your container start up in under a second, use 80% less memory, and pass security audits without breaking a sweat, you'll never go back.
Your Next Steps
Ready to give DHIs a shot? Here's what I recommend:
- Pick one service - Something simple, maybe an internal API
- Create a branch -
feature/migrate-to-dhi - Follow the migration steps above
- Run your tests - They should all pass
- Check the metrics - Image size, CVE count, startup time
- Share your results - Tweet me @ajeetraina, I'd love to hear about it!
Quick FAQ
Q: Can I use DHIs with Kubernetes? Absolutely! They work everywhere Docker works. I run them on EKS, GKE, and even on my Raspberry Pi cluster.
Q: What about debugging without a shell? Use kubectl debug, remote debugging, or good old logging. You don't need a shell in production, trust me.
Q: How often are DHIs updated? Continuously! Critical patches usually land within 24-48 hours. Docker handles this, so you just pull the latest.
Q: Can I build my own hardened images? Sure, but why reinvent the wheel? Docker's done the hard work. Focus on your app instead.
Q: Will this work with my CI/CD pipeline? 100%. No special tools needed. If you can build regular Docker images, you can use DHIs.
Wrapping Up
Docker Hardened Images aren't just another security tool - they're a fundamental shift in how we think about container security. Less is more. Minimal is powerful. Security by subtraction, not addition.
I've seen teams transform their entire security posture by adopting DHIs. Zero-CVE containers aren't a dream anymore - they're a docker pull away.
Give them a try this week. Start small. Measure the difference. I guarantee you'll be impressed.
And hey, if you run into issues or have questions, drop by our Collabnix Slack community. We've got 11000+ members who love talking about this stuff!
Until next time, keep shipping secure containers! 🚀
Found this helpful? Follow me on Twitter for more Docker tips and tricks.