Why Developers Are Moving to Docker Hardened Images (DHI)?
What if securing your containers was as simple as changing one line in your Dockerfile? Docker Hardened Images—now free for everyone—delivers zero-CVE base images and 95% smaller (distroless approach) while maintaining full compatibility with your existing workflows.

The Big Announcement
Docker made a bold move. Docker took the entire catalog of Docker Hardened Images—over 1,000 of them—and made them completely free.
It's what Docker calls a "fundamental reset" of the container security market. And it matters more than you might think.
The Industry Is Already Moving
This isn't just talk. Real projects are migrating right now.
Cloud Native Infrastructure:
- n8n (⭐53K+ stars, workflow automation platform) successfully switched from node:alpine to dhi.io/node:alpine3.22-dev
- Argo CD (⭐18K+ stars, CNCF graduated GitOps for Kubernetes) is exploring DHI adoption for their container images
- Renovate (⭐17K+ stars, automated dependency updates) is discussing DHI migration - this could accelerate ecosystem-wide adoption
- Harbor (⭐24K+ stars, CNCF graduated cloud native registry) is evaluating DHI migration for their container images
- nginx-proxy (⭐18K+ stars, automated nginx reverse proxy for Docker) is discussing DHI adoption for their base images
- cupdate (container update tool) is migrating to DHI for automated container updates
- KubeArmor (⭐1.5K+ stars, Kubernetes runtime security) is exploring DHI adoption for enhanced container security
Enterprise Cloud Providers:
- Apache Airflow (⭐39K+ stars, major orchestration platform) is busy migrating their images to DHI
- Azure Container Registry (ACR) (Microsoft's managed container registry) is evaluating DHI support for their platform
- Medplum (⭐1.8K+ stars, healthcare platform) migrated to DHI for their open-source healthcare infrastructure
- AWS is tracking Docker Hardened Images adoption in their container roadmap
Database Infrastructure:
- ParadeDB (⭐6K+ stars, PostgreSQL for search and analytics) is migrating to DHI for their database containers
Energy & Blockchain:
- Energy companies like ENECHANGE are switching their infrastructure to hardened base images
- Blockchain projects like Ethereum's Optimism monitoring tools are making the move
Security & Developer Tools:
- Cyberbro (threat intelligence platform) is transitioning to DHI for better security posture
- Hetzner DDNS is adopting hardened images for DNS management infrastructure
- Even gaming communities—like the Deadlock mod manager project—are adopting hardened images
From enterprise infrastructure to open-source gaming tools, developers are voting with their issues and pull requests. The migration is happening. The momentum is real. And it's accelerating.
Why This Matters Right Now
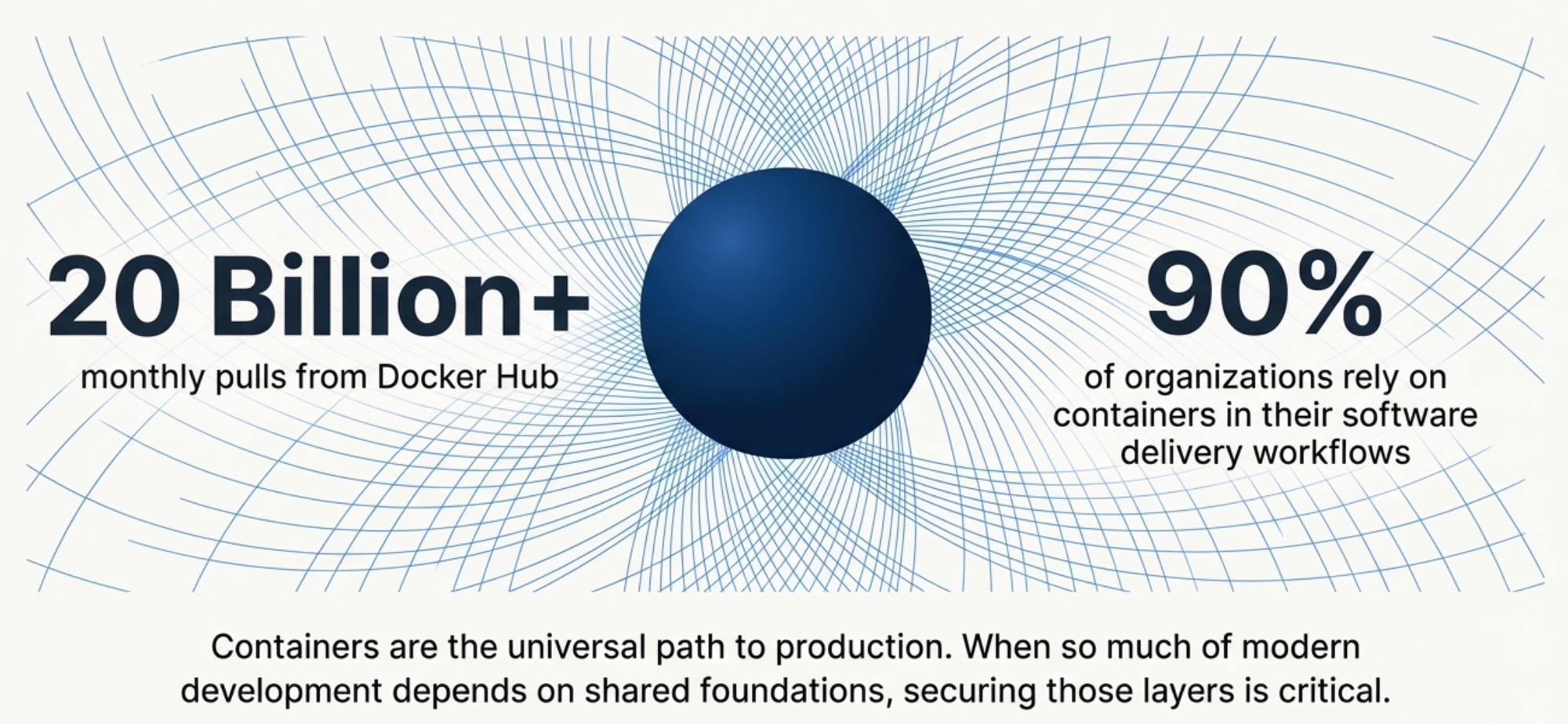
The software supply chain starts at the base layer—your container images. If your foundation is compromised, everything you build on top is at risk. Docker just made securing that foundation accessible to everyone.
What Are Docker Hardened Images?
Think of regular container images as a house with unlocked doors and windows. Sure, you can lock them yourself. But what if they came pre-secured from the factory? That's Docker Hardened Images.
Less Is More
Traditional community images are bloated. They include shells. Package managers. Utilities you never use. These extras are convenient. But they're also tools attackers can use against you. DHI strips all that away. It's called a "distroless" approach. You get only what your application needs to run. Nothing more.The result? Up to 95% smaller (distroless approach) and secure defaults without ever compromising transparency or trust.
Built on Trust, Not Opacity
Here's where Docker does something different.
Some vendors hide their vulnerability data. They use proprietary scoring systems. Everything looks "green" in their scanners.
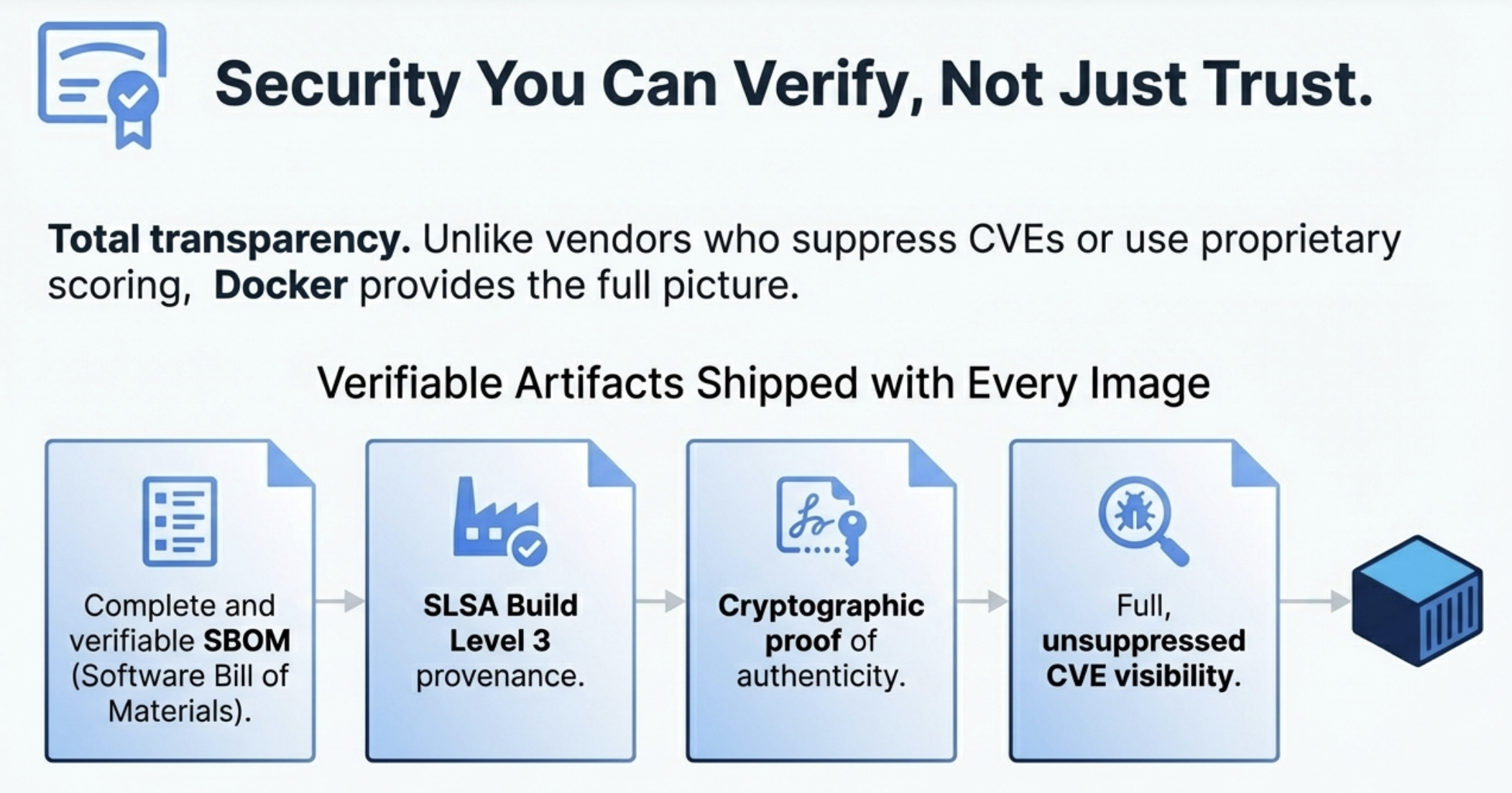
Docker gives you 100% transparency. Every hardened image comes with three critical pieces of evidence:
- Full SBOM (Software Bill of Materials)
This is a complete inventory of every component in your image. Every library. Every dependency. Everything. You can verify exactly what you're running.
- SLSA Build Level 3 Provenance
This is cryptographic proof. It proves the image was built on secure infrastructure.It proves nobody tampered with it between build and deployment.
- Cryptographic Authenticity
When you pull a hardened image, you know it's exactly what Docker built. No substitutions. No modifications. No compromises.
The Technology Behind It
- Distroless Runtimes
These images are minimal by design. No shell access. No package managers. No debugging tools. If an attacker breaks in, they have nowhere to go. No tools to work with. Your application runs. Everything else is stripped away.
- Open Source Foundations
DHI isn't built on proprietary systems. It uses trusted distributions like Debian and Alpine. This means compatibility with both glibc and musl environments. Translation? You can drop these images into your existing workflows with minimal changes.
- Continuous Security Updates
The images aren't static. Docker maintains them through an event-driven build system. When a vulnerability is discovered, patches roll out automatically. You get near-zero vulnerability postures without lifting a finger.
Migration Made Easy
Switching to hardened images used to be manual work. Docker solved this with AI assistance. Their AI assistant scans your existing containers. It recommends the equivalent hardened image. It can even apply the changes automatically.
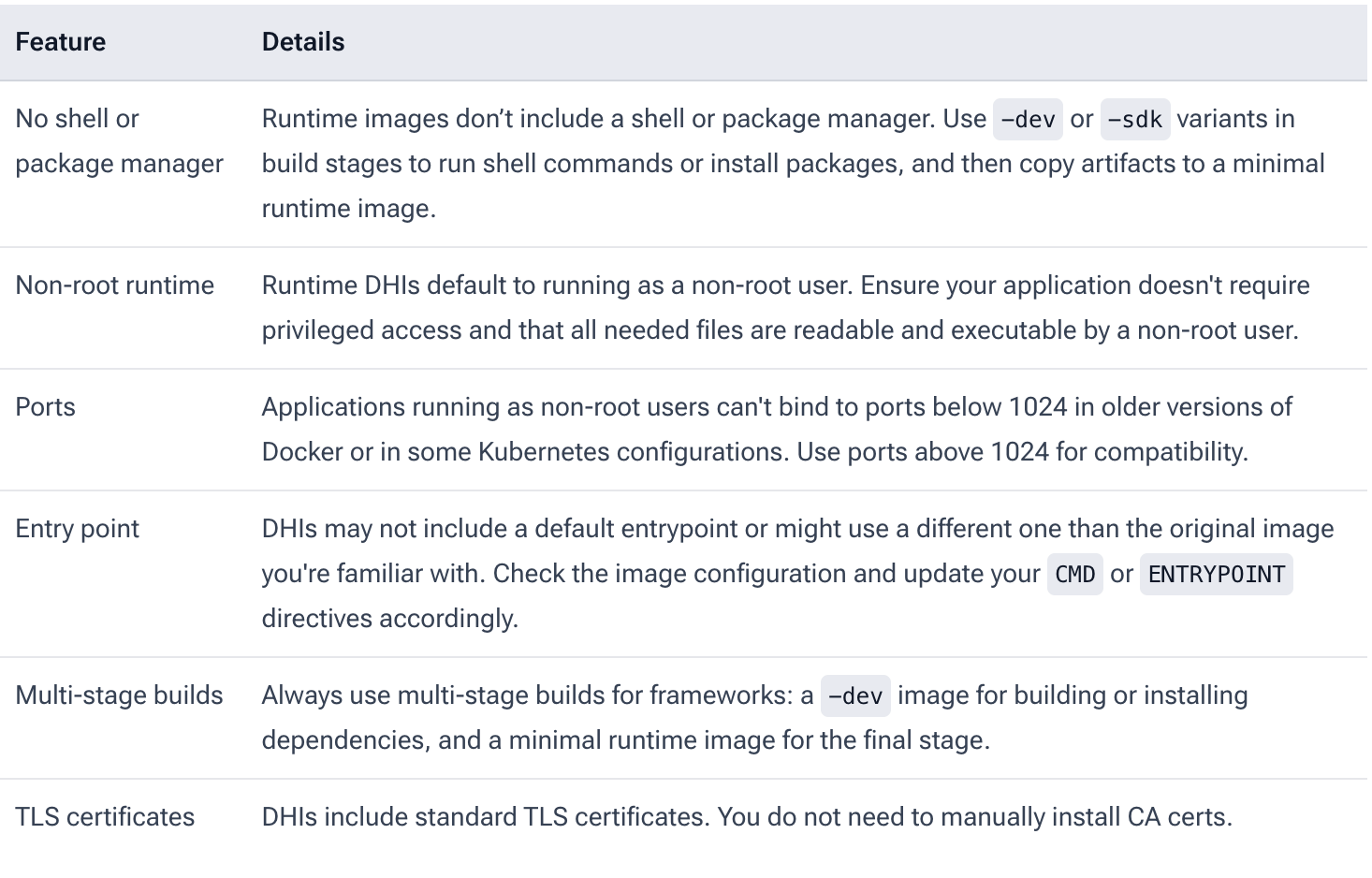
If you're planning to update the existing Dockerfiles or frameworks manually to use DHIs, keep the following considerations in mind.

A Real Example
Here's what migration looks like:
# Before (Standard Python Image)
FROM python:3.11-slim
WORKDIR /app
COPY . .
RUN pip install --no-cache-dir -r requirements.txt
CMD ["python", "app.py"]# After (Hardened Python Image)
FROM dhi.io/python:3.11-debian
# DHI encourages security best practices
USER 1001
WORKDIR /app
COPY . .
# DHI preserves essential build tools
RUN pip install --no-cache-dir -r requirements.txt
CMD ["python", "app.py"]One line changed. Security dramatically improved. That's drop-in adoption.
Securing the AI Layer
AI agents are everywhere now. They're writing code. Managing infrastructure. Accessing your data. But AI introduces new attack vectors.
The MCP Problem
The Model Context Protocol (MCP) connects AI assistants to external data sources. It's powerful. It's also a potential security nightmare. Docker saw this coming.
Hardened MCP Servers
Docker applied the same hardening principles to MCP servers. Popular servers like MongoDB, Grafana, and GitHub now have hardened versions. Minimal footprints. Provenance attestations. Full transparency. This prevents data exfiltration. It blocks supply chain attacks in AI workflows. Your AI agents can be as secure as your applications.
Free vs. Enterprise: Your Choice
The core catalog is completely free. Apache 2.0 license. Use it anywhere. Modify it as needed. But some organizations need more.
DHI Enterprise Features
Enterprise customers get additional guarantees:
- SLA-Backed Patching Critical CVEs are fixed in under 7 days. Docker is working toward 24-hour SLAs.
- Compliance Variants FIPS-enabled images. STIG-ready configurations. CIS benchmark compliance.
- Extended Lifecycle Support (ELS) When upstream distributions stop getting updates, Docker keeps patching.
Five additional years of security coverage.This protects long-lived production systems that can't easily migrate.
The Bigger Picture

Docker isn't doing this alone. Industry giants are on board. Google Cloud supports these images. MongoDB integrates them. The CNCF endorses them. This creates a unified ecosystem.
What This Means for Developers
Security used to be hard. It required expertise. Time. Money. Now the secure choice is also the easy choice. You pull a hardened image. You build your application. The foundation is secure by default. No extra work required.
Wrapping Up
Docker just eliminated the excuse for insecure foundations. The hardened images are free. They're easy to adopt. They're maintained continuously. Security starts at the base layer. And now that base layer is accessible to everyone. From solo developers to Fortune 500 companies. From hobby projects to mission-critical infrastructure. The right thing to do is now the easy thing to do. That's how you change an industry.
Ready to get started? Visit Docker Hub and search for "hardened" images. Your first secure foundation is just one docker pull away.
Want to learn more? Check out the Docker Hardened Images documentation for implementation guides, best practices, and migration strategies.